

Platform
Bipsync Core
Investment research management software (RMS) designed to bring your research within reach in every investment decision.
From fragmented data and lost notes to a single, scalable platform tailored to how investment teams actually work.
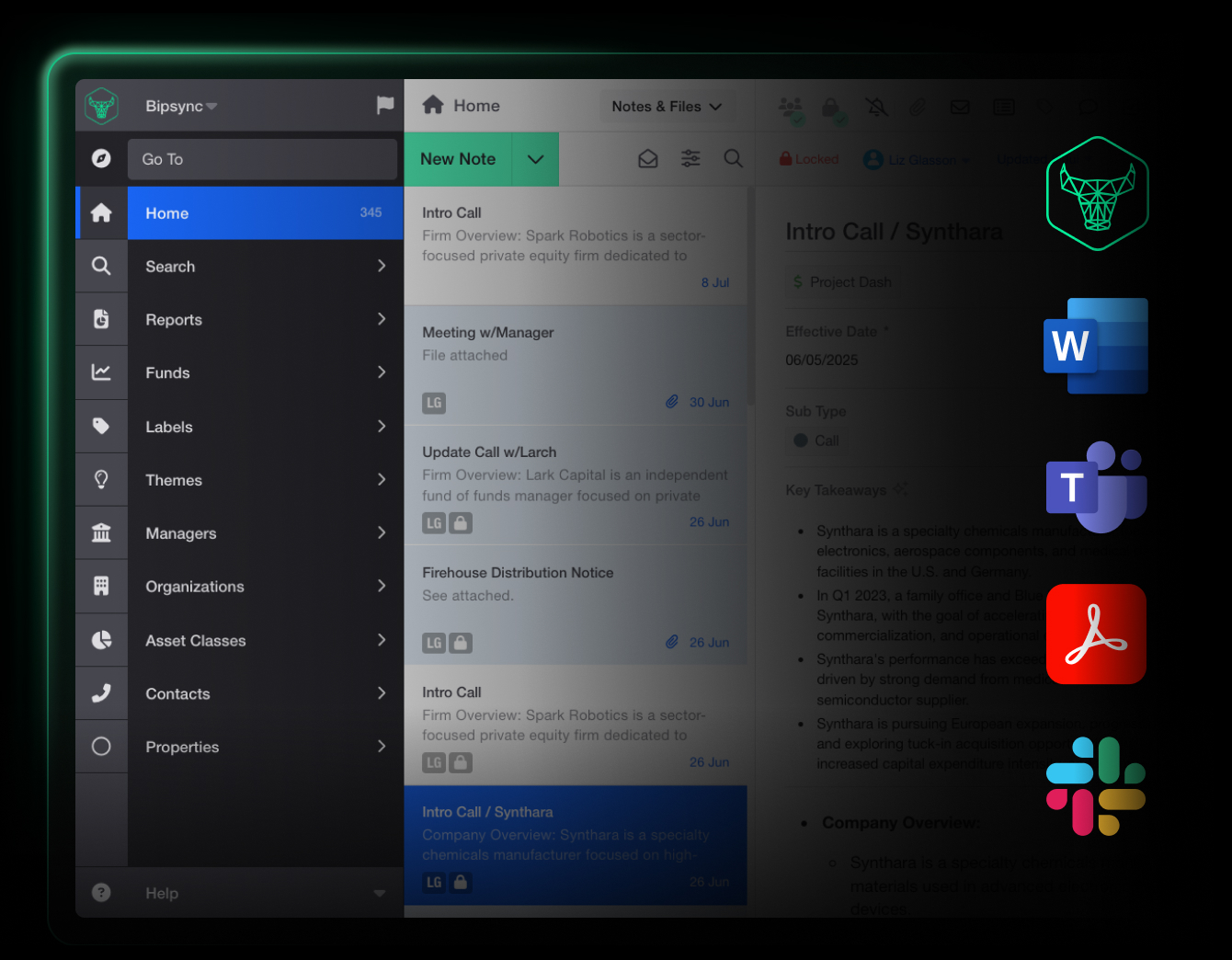
Centralized research, tailored to you
Outcome
Save time and eliminate scattered workflows.
How
Replace shared drives, spreadsheets, and stored emails with a structured, searchable platform built for investment teams.
Built-in note-taking, custom tagging, version control, and advanced search make it easy to find what matters
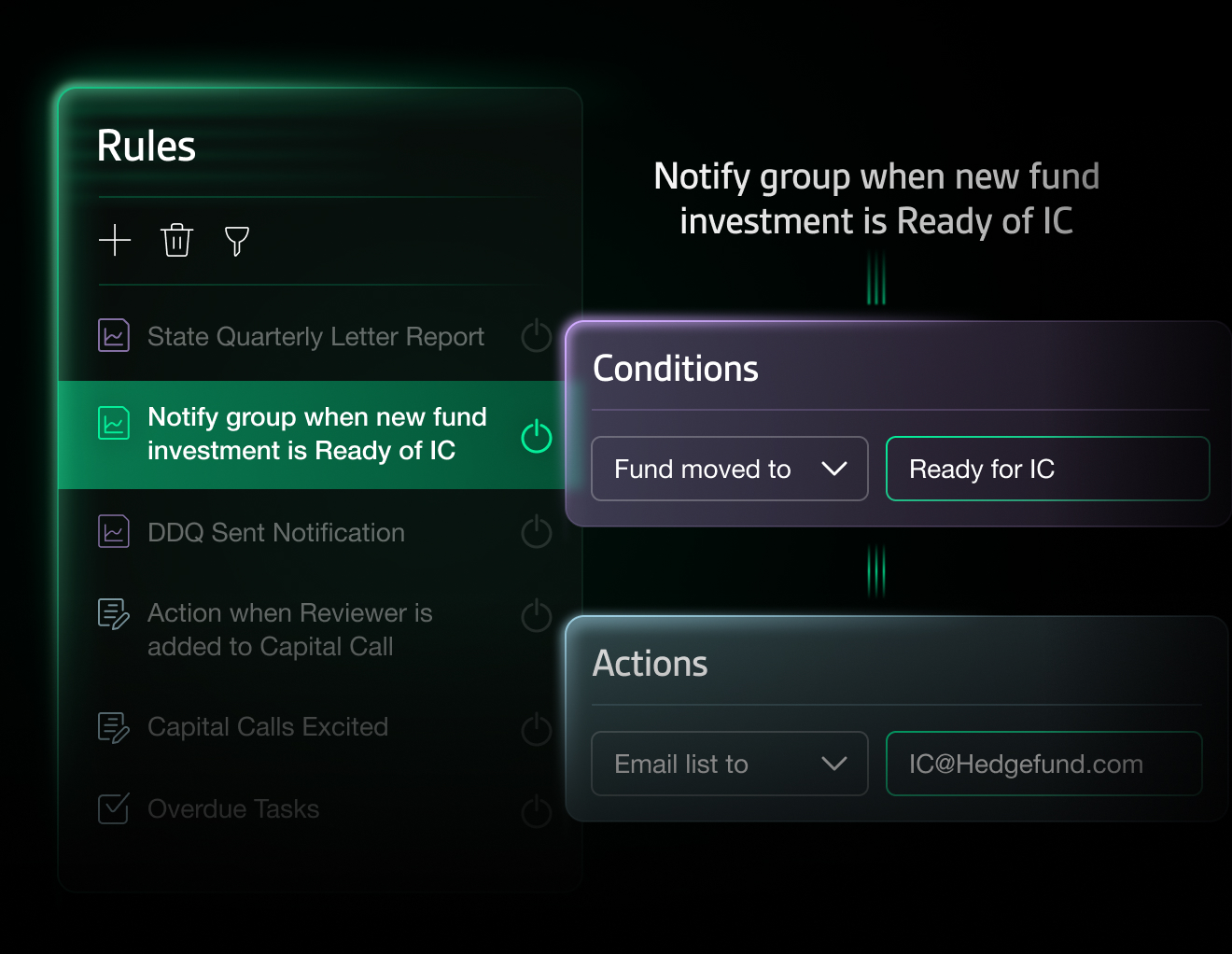
Run complex
workflows, simply
Outcome
Scale without adding headcount.
How
From idea to investment, Bipsync gives you structured workflows, dashboards, and automation rules that flex with your needs.
Use templates or build your own, from IC prep to manager due diligence pipelines
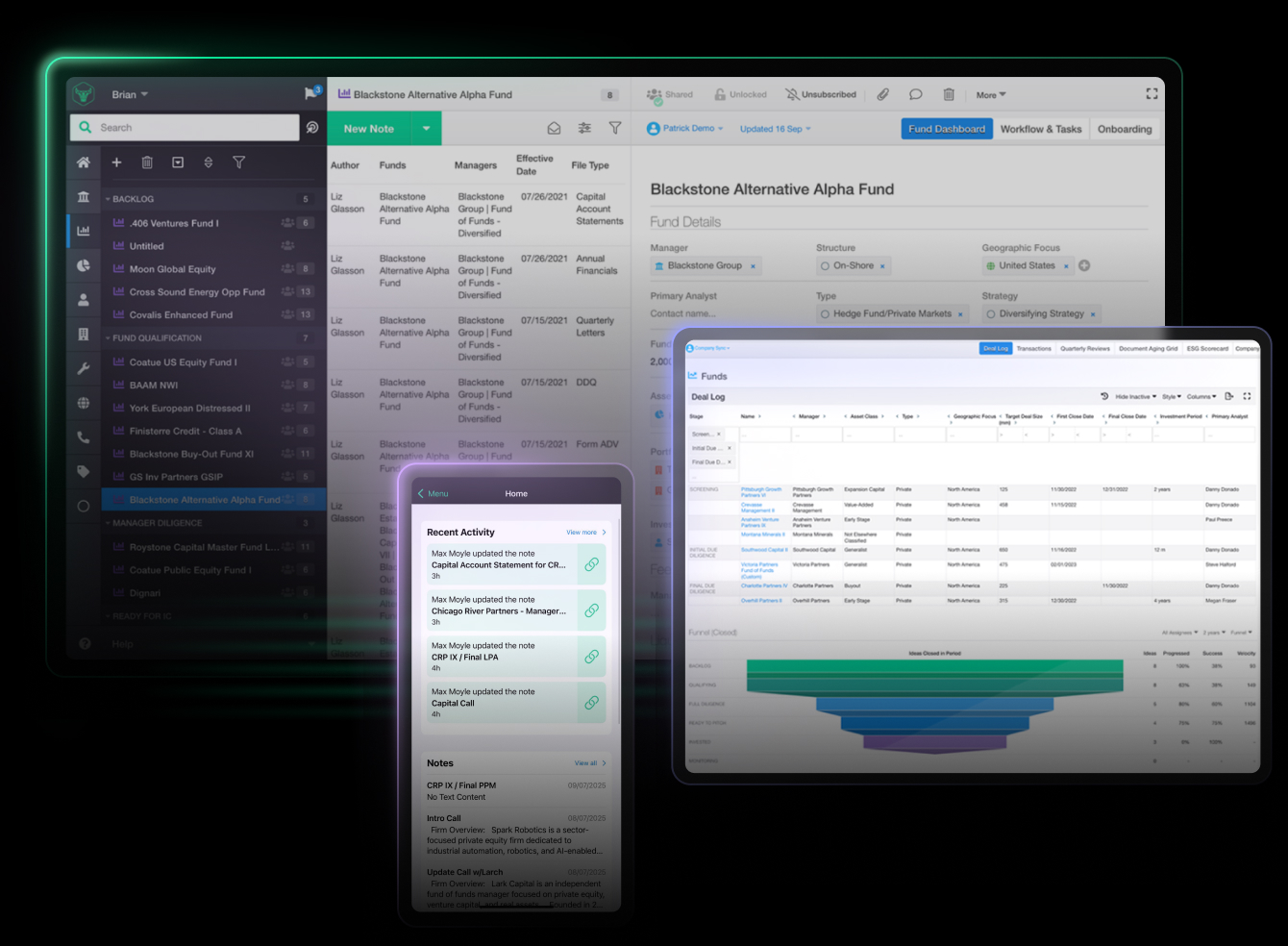
Stay in sync,
wherever you work
OUTCOME
Keep your team connected and productive on any device.
HOW
A consistent experience across desktop, web, and mobile, with full offline support.
No more emailing PDFs or hunting through chat logs. Notes, files, and updates flow in real time.
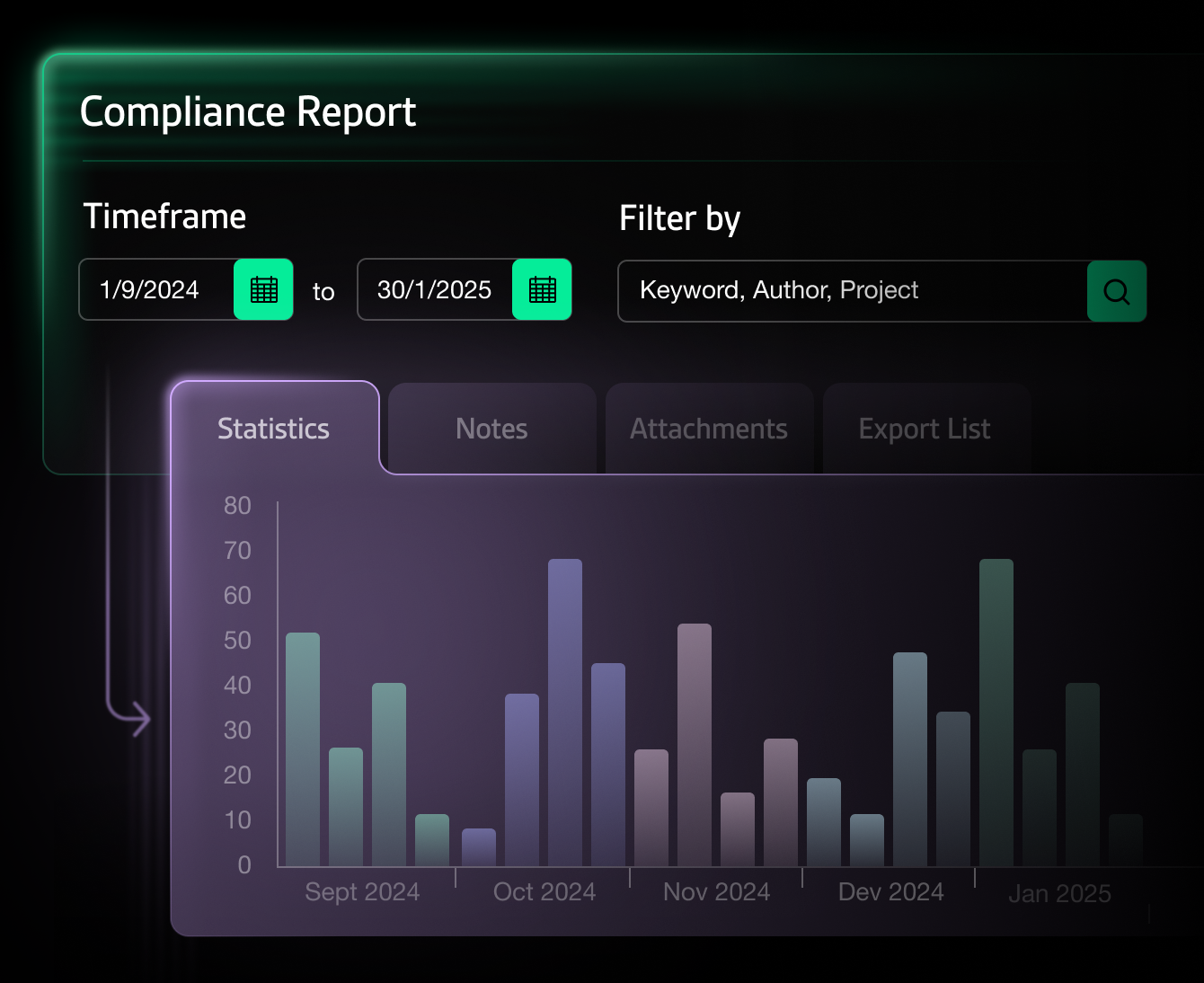
Drive governance,
compliance, and oversight
OUTCOME
Be audit-ready at any time.
HOW
Bipsync captures a full digital footprint of your research, with fine-grained permissions, record-keeping, and easy discovery.
Achieve SEC/ESG compliance standards with confidence, and user adoption to match.

Integrate, don’t overhaul
OUTCOME
Plug into your existing tech stack and eliminate silos.
HOW
Our open API, secure integrations, and dedicated onboarding team make rollout simple.
From portfolio systems to third-party data feeds—your research flows with everything else.





Built for teams like yours


Security
Bipsync is committed to safeguarding client data through robust security practices aligned with SOC 2 and ISO 27001 standards. We enforce strict controls across data separation, encryption, and access management.
Data Separation: Each client’s data is stored in a dedicated, single-tenant environment, never co-mingled with others.
Encryption: Data is encrypted in transit (TLS) and at rest (AES-256), including all backups.
Access Control: Granular permissions and full audit logs ensure secure, compliant access.


